Why You Should Comply With CIS
In the past few years, there have been numerous examples of how poorly configured systems have paved the way for hackers. These examples have also led to regulatory bodies imposing hefty fines for improper conduct.
Fortunately, there are prescriptive guidelines, provided by the Center for Internet Security (CIS), for establishing a secure baseline configuration for assets to prevent poorly implemented configurations. CIS Benchmarks are the only independent, consensus-based, and industry-accepted guidelines for configuration best practices that have been developed by a global community of cybersecurity professionals and academics from all walks of life and are accepted by governments, businesses, industries, and the wider academic community.
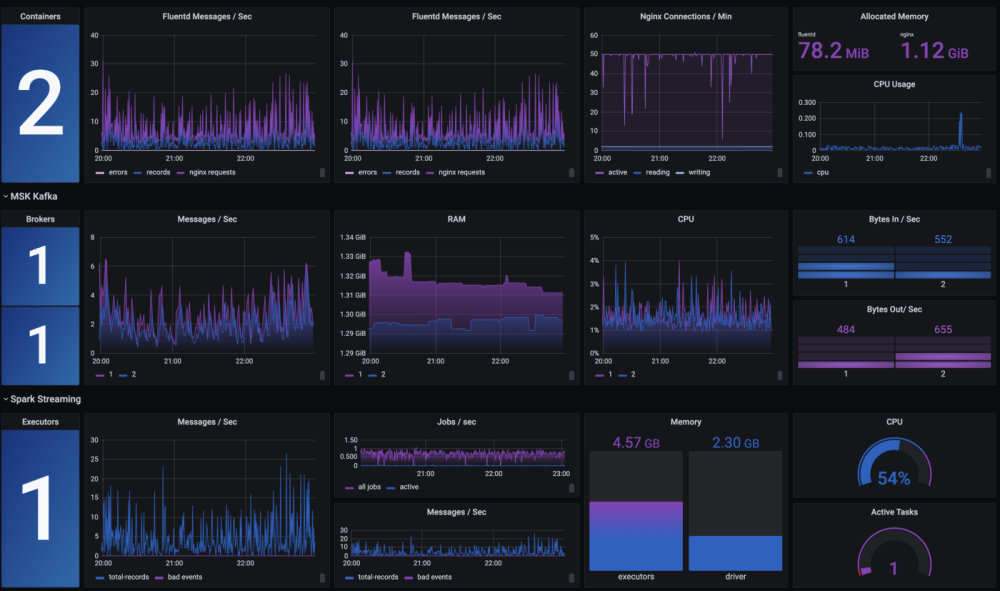
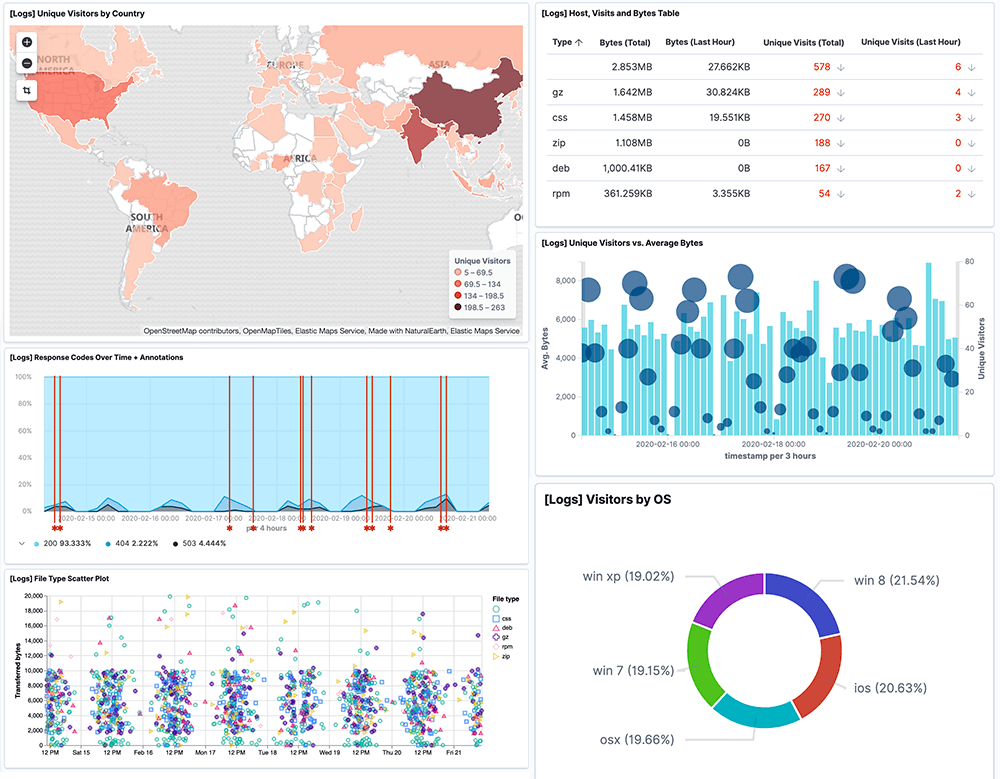
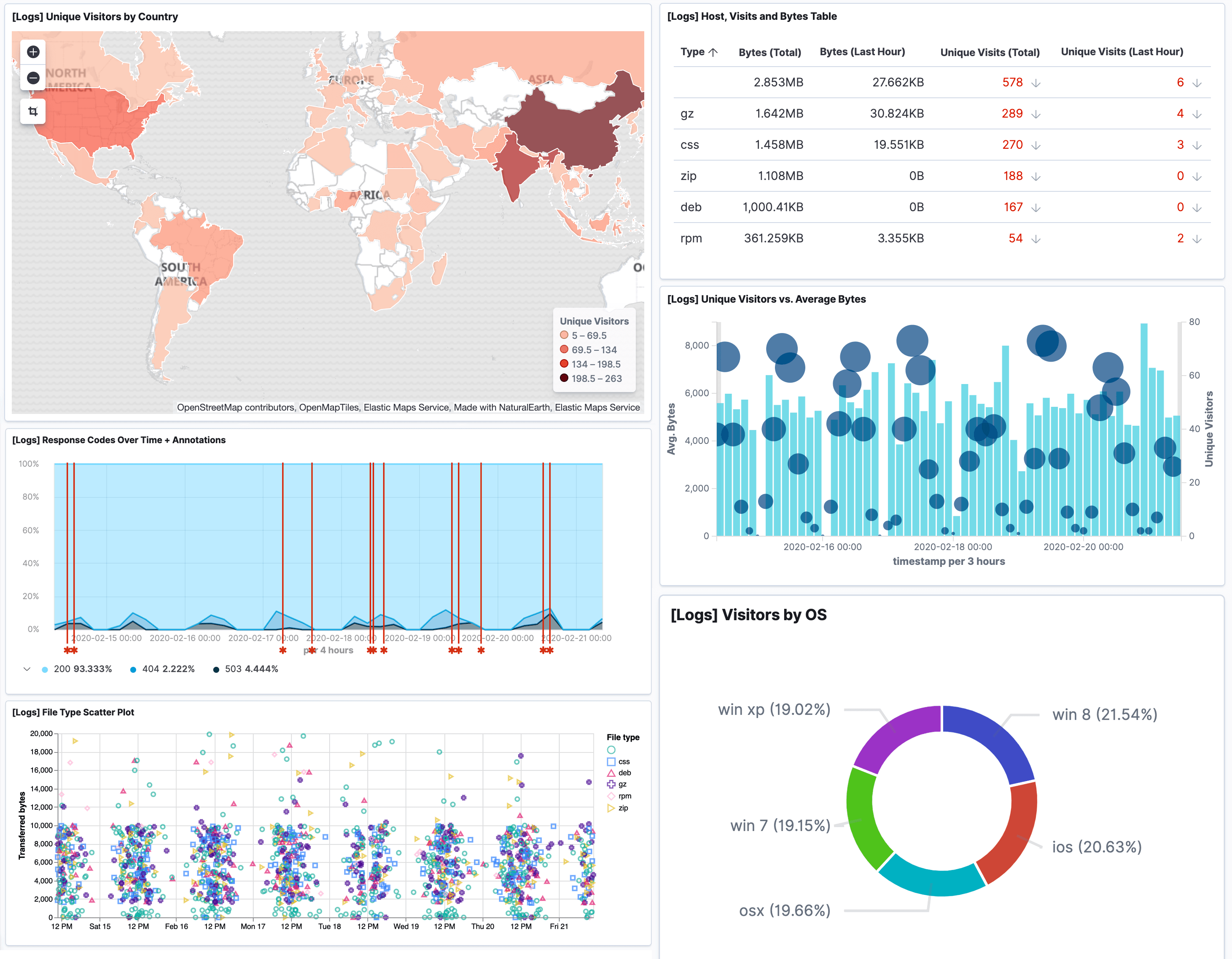
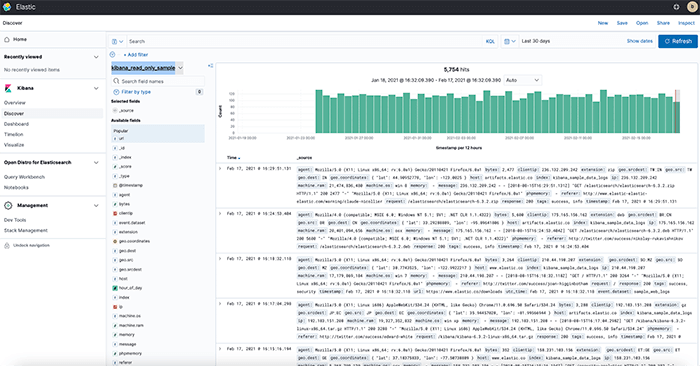
If you want to manually assess all your endpoints, network devices and operating systems within a highly distributed system architecture, it is worth knowing that these benchmarks run about 800 pages on average and make over 300 recommendations within them. With all of these guidelines to comply with a solution that can meet at least ten of these controls can save your engineers many hours from having to manually centralise data.
As a result, The Logit.io platform has become an essential tool in the vulnerability management process for centralising logs, events and traces. Monitor your endpoints for any CIS control violations and make corrective actions in real time by leveraging the Logit.io CIS compliance solution. With Logit.io‘s extensive CIS compliance features, the platform can be used to meet various critical controls including 8.1, 8.2, 8.3, 8.5, 8.6, 8.7, 8.8, 8.9, 8.10, 8.11 and 8.12.