What Is HIPAA?
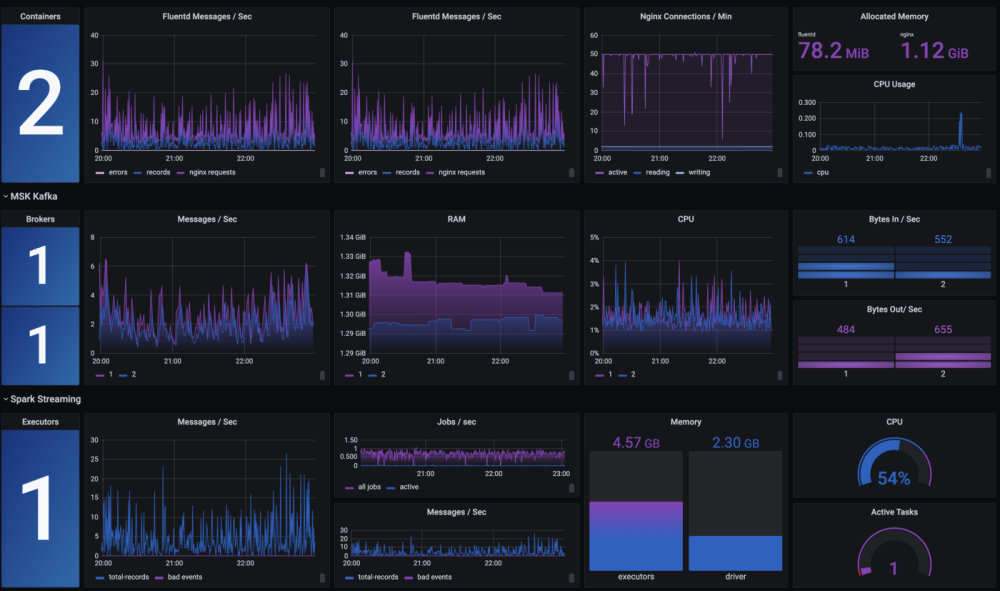
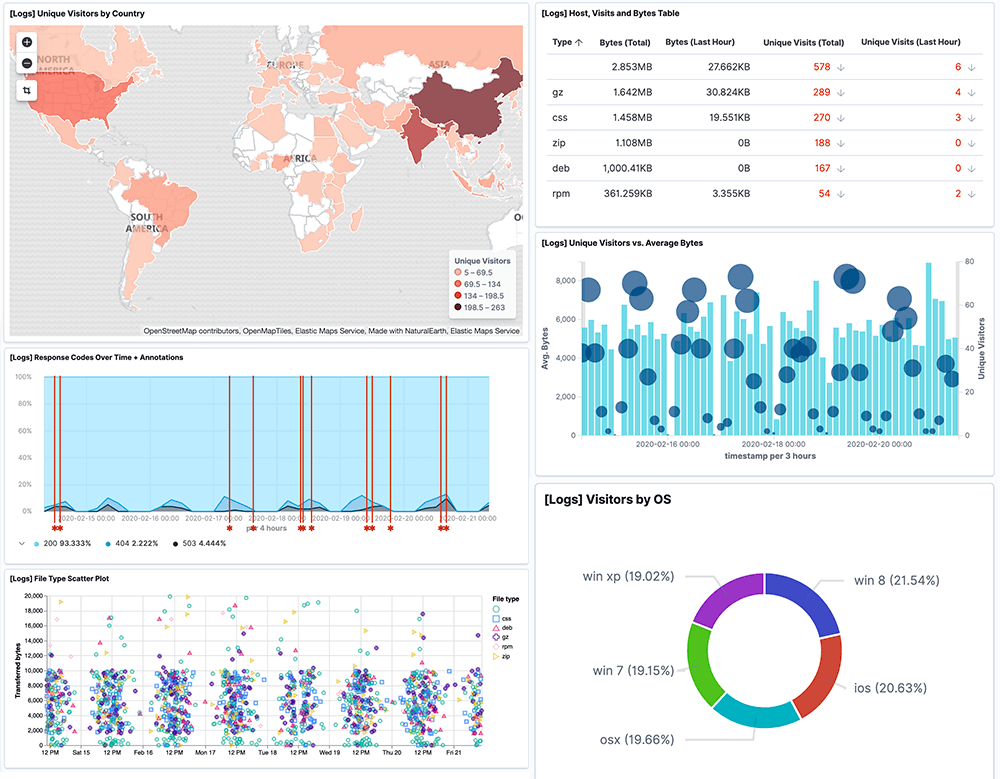
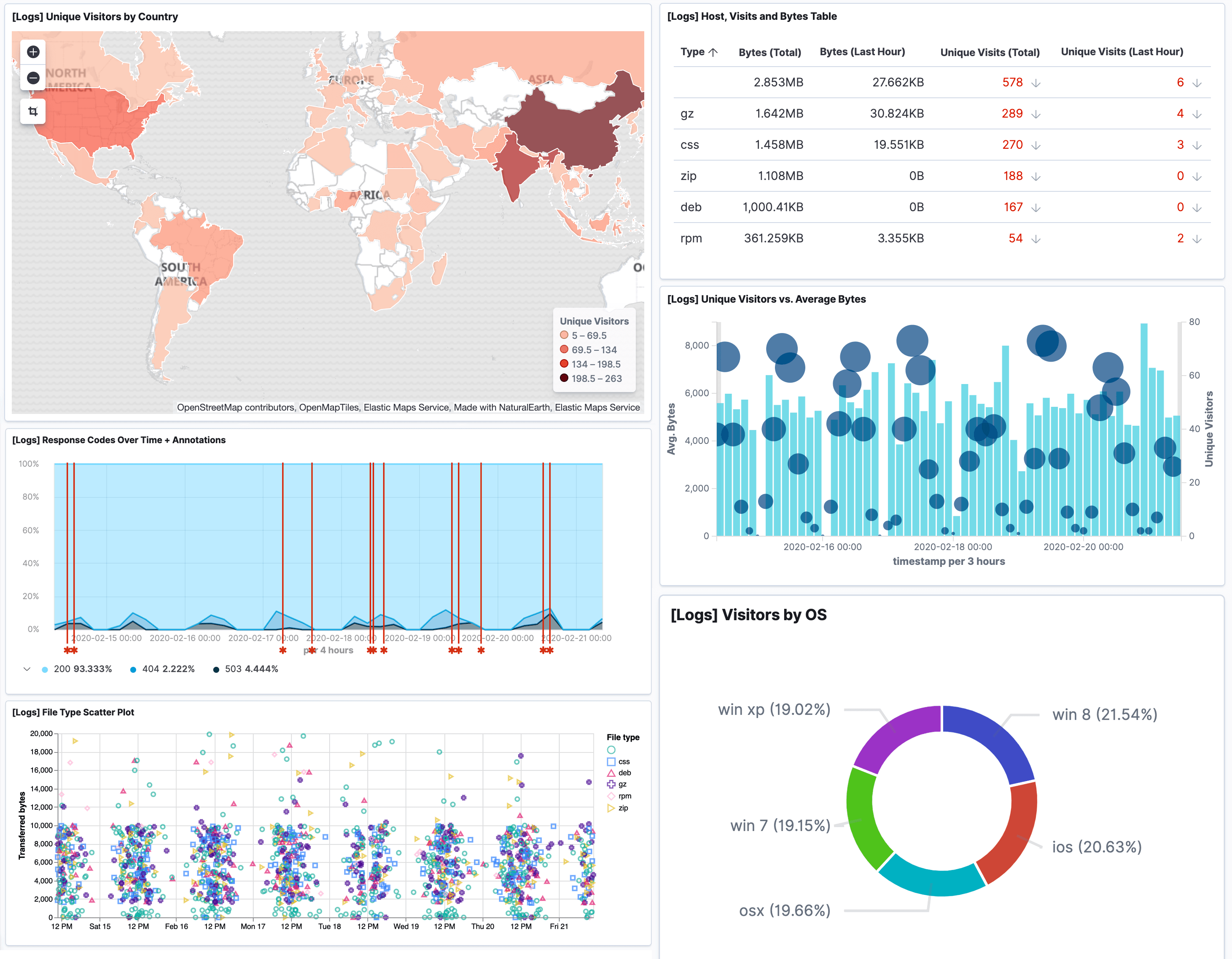
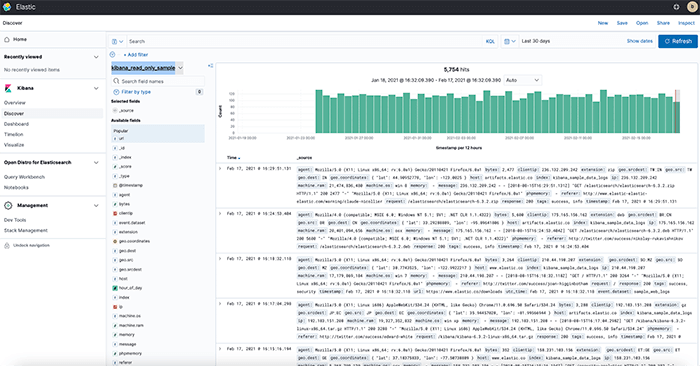
HIPAA is an acronym for Health Insurance Portability and Accountability Act. The law was passed in 1996 and is designed to protect the privacy and security of personal health information (PHI). Information about an individual‘s health, such as diagnoses, treatments, and payments, is considered PHI.
As part of HIPAA, national standards are established for the privacy and security of PHI, and guidelines are set for how covered entities must handle and protect this information. There are several key provisions in HIPAA, including the right of patients to access their own health records, restrictions on the use and disclosure of PHI, and the requirement that covered entities implement administrative, physical, and technical safeguards to prevent unauthorized access to and disclosure of PHI.