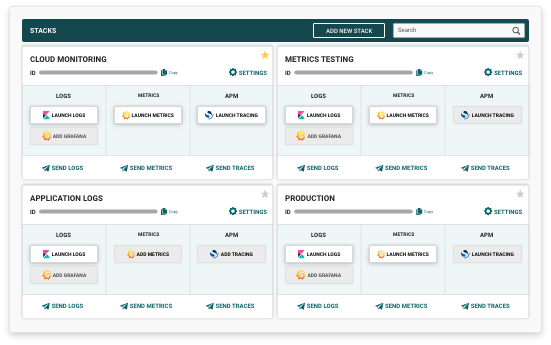
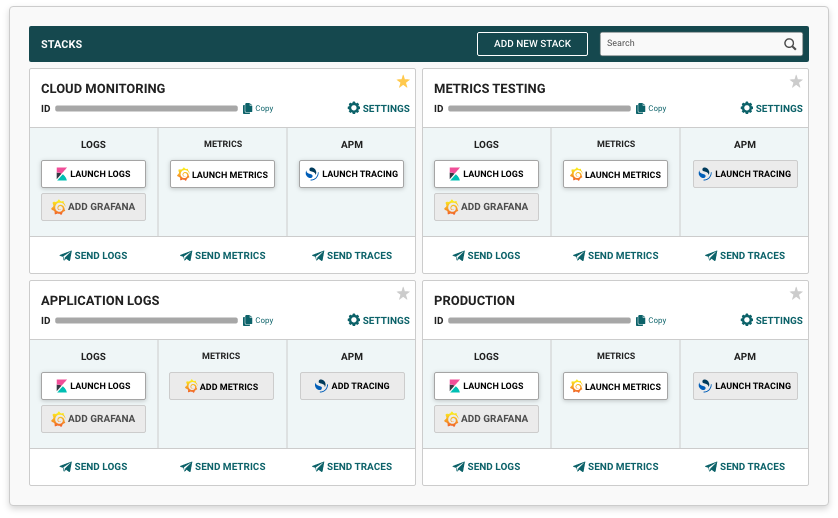
With Logit.io, logs are stored in a centralised location, controlled by access controls and retained for the appropriate period of time. Managing logs in this way can help organizations meet NCSC CAF requirements.
The log analysis and reporting capabilities provided by Logit.io make it easy for organisations to analyse and report on log data to detect anomalies, identify potential security incidents, and ensure compliance with security policies and regulations.
Real-time alerts and notifications can also be configured for Logit.io based on specific log events or thresholds. As a result, organisations can respond quickly to potential security incidents and meet NCSC CAF incident management requirements.
Log management is crucial to complying with the NCSC's Cyber Assessment Framework (CAF). Using Logit.io, organisations can meet NCSC CAF requirements for log collection, storage, analysis, and reporting with a powerful and scalable log management solution. Using Logit.io, you can collect and store logs from a wide variety of sources and analyse log data to detect potential security incidents.
It is important to note that while Logit.io can be a useful tool for supporting NCSC CAF compliance, the compliance process ultimately also requires policies, procedures, and technical controls to be put in place.