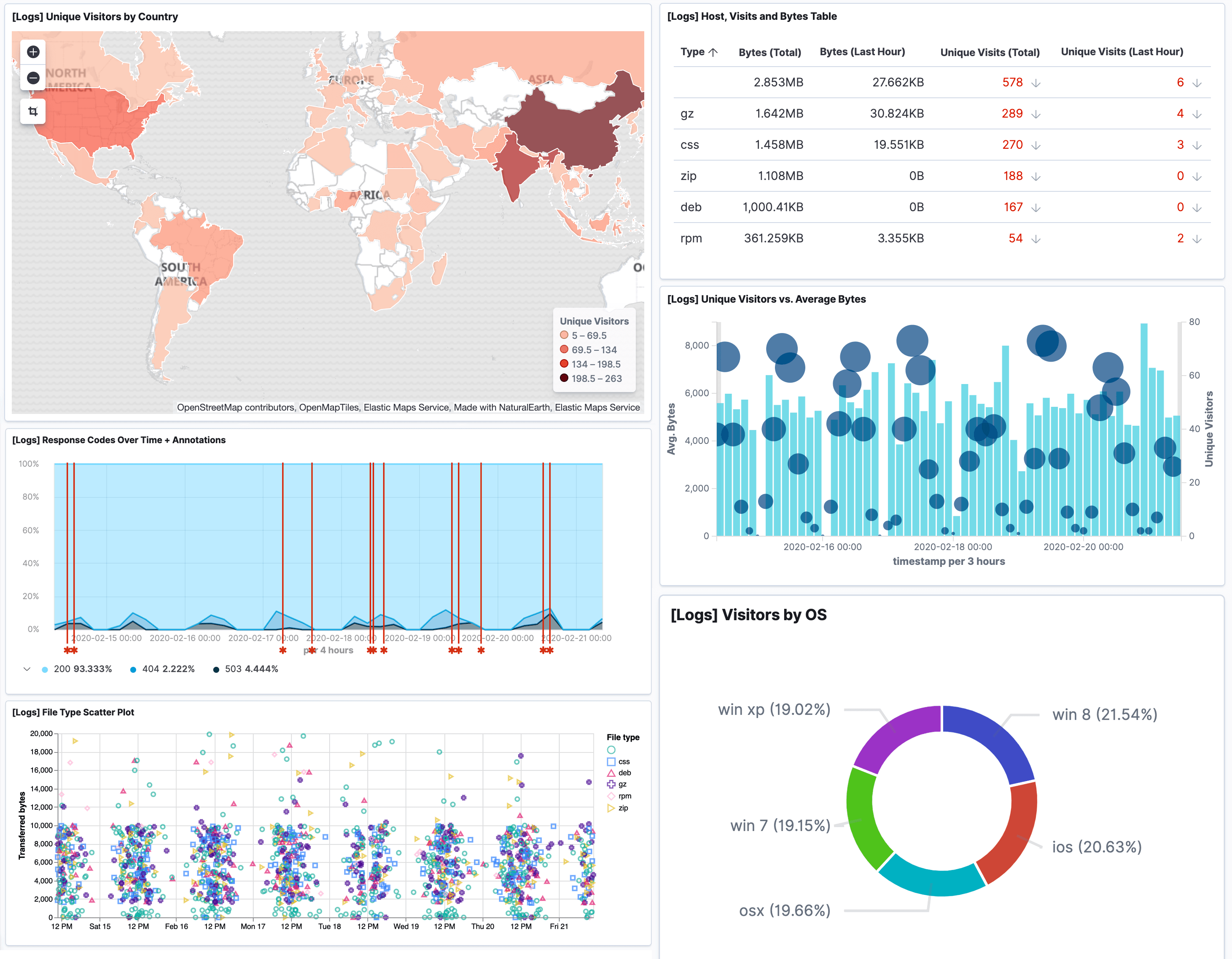
Security log management is the process of gathering, analysing and visualising information about security events such as intrusions or suspicious activity occurring on networked systems and infrastructure. Security log management helps an organization to monitor its networked assets (e.g., servers, workstations, hardware devices) with the aim of discovering evidence of malicious attacks and hacking attempts in real-time.
This analysis enables the organization to take responsive action against threats before they do extensive damage or expose valuable information.
Logit.io's security log management provides a critical component of your security architecture by processing and collecting information from various applications and systems so that you can review this data for anomalies and alert your administrators when a suspicious event is detected.
The principal objective of security log management is to provide monitoring and alerting capabilities that allow organisations to detect malicious activity and prevent any data breaches or other data corruption.
These capabilities also help organisations to implement automated and dynamic approaches to their information security posture and governance, as well as provide tools for network monitoring, infrastructure forensics, compliance reporting, incident response investigations and more.
The first step to protecting your organization's assets and data is to acquire and implement a security log management solution such as the one provided by Logit.io.