Security, Resources
5 min read
Taking proactive actions regarding the security of your systems is a fundamental part of all organizations. It's impossible to predict what cyber attacks or incidents your organization may face but there are solutions and options available to you that assist in detecting threats before they can impact your organization.
One of these valuable solutions is security analytics. With security analytics, you can attain numerous capabilities to proactively rectify incidents and cross-communicate your cybersecurity team. With effective monitoring and analysis tools that security analytics provides you can guarantee that your organization is in the best position to detect potential threats as they occur.
Security analytics is particularly valuable in today's world, with hackers using a broad variety of attack strategies targeting numerous vulnerabilities. Some of these threats can easily go unnoticed for long periods.
Within this article we will define what security analytics is, the difference between security analytics and SIEM, as well as list the advantages and use cases of security analytics.
Contents
What is Security Analytics?
Security analytics is the use of data collection, aggregation, and analysis tools and techniques to locate, prevent, and react to security threats. It entails analyzing data from numerous sources within an organization’s IT infrastructure to highlight patterns, anomalies, and indicators of potential security incidents. The main objective of security analytics is to improve the overall security posture by offering actionable insights that can be used to mitigate risks and protect against cyber attacks.
Security Analytics vs SIEM
SIEM (Security Information and Event Management) is the collection, examination, and correlation of security-related data from multiple sources within an organization’s IT infrastructure. The main goals of SIEM are to detect security threats, manage security incidents, and ensure compliance with regulatory requirements. From this definition, it appears similar to security analytics, which it is, but there are key differences.
Firstly, security analytics utilizes advanced techniques to examine and interpret data, this provides you with deeper and more sophisticated insights, enabling more accurate decision-making. In contrast, SIEM focuses on real-time data aggregation and correlation to highlight and alert on security incidents. As well as this, in general, security analytics can be viewed as a proactive solution, aiming to predict and prevent future threats and SIEM is reactive in that it focuses on real-time detection and response to current threats.
Whilst these tools have key differences that can lead users to choose one solution over the other, there are benefits to using the two solutions together. Security analytics can enhance SIEM capabilities by offering advanced threat detection and deeper analysis and SIEM offers the foundational data and real-time monitoring capabilities that security analytics can build upon.
Security Analytics: Advantages
By utilizing security analytics you can attain numerous benefits that will enhance your organization's ability to protect its digital assets and respond to threats. Firstly, security analytics excels at highlighting sophisticated and evolving threats that traditional security measures may miss. By utilizing advanced techniques such as machine learning, behavioral analysis, and anomaly detection, security analytics can highlight patterns and irregularities that indicate potential security breaches. This capability is particularly important for detecting advanced persistent threats (APTs) and zero-day vulnerabilities, which frequently elude signature-based detection methods.
In addition, another key strength of security analytics is the extensive visibility into your organization's IT environment that it provides. The solution aggregates and examines data from a broad range of sources such as application logs, network traffic, and user behavior, providing a unified view of your entire security landscape. With this holistic perspective, your security team can better understand the context and scope of potential threats.
Continuing with the advantages offered by security analytics, another is that security analytics supports your organization in adhering to compliance regulations. The solution will continuously monitor and examine security-related data, ensuring that your organization maintains the required logs and generates comprehensive reports that are required for audits. This capability not only streamlines the compliance process but also offers a clear and documented trail of security activities, which is crucial for demonstrating due diligence and accountability.
Lastly, security analytics offers numerous predictive capabilities that can provide enhanced decision-making and strategic planning. Recognizing potential threats and vulnerabilities before they are exploited, means that security analytics offers your organization the information required to prioritize your security efforts and allocate resources more effectively. This forward-looking approach aids in developing a proactive security posture, lessening the likelihood of successful attacks.
Security Analytics: Use Cases
Security analytics can be effectively utilized for a wide array of use cases, one of these being threat detection and prevention. Security analytics can detect and prevent multiple types of cyber threats. Examining network traffic, endpoint logs, and user behavior in real-time, ensures security analytics systems can highlight suspicious activities and anomalies indicative of potential security breaches. This proactive approach aids organizations in mitigating risks before they escalate into significant incidents.
Also, security analytics is an ideal solution for anomaly and intrusion detection, as the tool will establish baseline behavior patterns and continuously monitor for any activity outside of these patterns, allowing the security monitoring system to rapidly detect potential intrusions or security breaches. This is critical for safeguarding sensitive information, infrastructure, and intellectual property from cyber threats.
In addition to the two examples mentioned above, security analytics excels at the following use cases:
- Insider Threat Monitoring
- Advanced Persistent Threat (APT) Detection
- Fraud Detection and Financial Crimes Monitoring
- Compliance Monitoring and Reporting
- Security Incident Investigation and Forensics
Leading Security Analytics Tools
Splunk
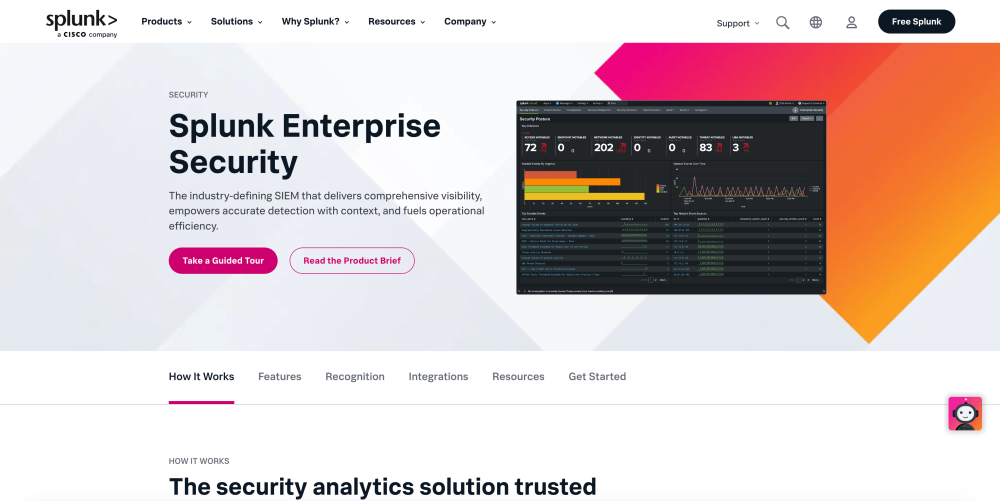 Splunk’s Enterprise Security tool is a widely used security analytics solution. Splunk, similar to numerous other vendors offering security analytics solutions, utilize AI to enhance their product. Assistive AI is intertwined into Spunk’s data-powered platform offering users visibility by seamlessly ingesting, normalizing, and examining data from any source and at scale.
Splunk’s Enterprise Security tool is a widely used security analytics solution. Splunk, similar to numerous other vendors offering security analytics solutions, utilize AI to enhance their product. Assistive AI is intertwined into Spunk’s data-powered platform offering users visibility by seamlessly ingesting, normalizing, and examining data from any source and at scale.
Logit.io
 Logit.io offers a powerful, cost-effective security analytics platform built on the ELK stack. Our managed ELK platform provides the backbone of our security analytics capabilities and is renowned for allowing security practitioners to engage in threat hunting, anomaly detection, cloud monitoring, and endpoint security, all within a single user interface provided by Kibana. Also, as the Logit.io security analytics platform is a managed solution you can gain all the essential features without concerning yourself with the cost of hosting, upgrading, and maintaining various open source security tools for your organization.
Logit.io offers a powerful, cost-effective security analytics platform built on the ELK stack. Our managed ELK platform provides the backbone of our security analytics capabilities and is renowned for allowing security practitioners to engage in threat hunting, anomaly detection, cloud monitoring, and endpoint security, all within a single user interface provided by Kibana. Also, as the Logit.io security analytics platform is a managed solution you can gain all the essential features without concerning yourself with the cost of hosting, upgrading, and maintaining various open source security tools for your organization.
If you’re interested in finding out more about the extensive features of Logit.io’s security analytics platform then feel free to contact us, or begin exploring the platform for yourself with a 14-day free trial.
LogRhythm
 LogRhythm's security analytics solution aims to help you and your team enhance detection accuracy and efficiency to facilitate smarter and faster decision-making. With this tool, you can attain real-time visibility into endpoint and server activities to surface cyber threats. As well as this, you can utilize network traffic behavior analytics to expose attacks that are targeting your networked systems and devices.
LogRhythm's security analytics solution aims to help you and your team enhance detection accuracy and efficiency to facilitate smarter and faster decision-making. With this tool, you can attain real-time visibility into endpoint and server activities to surface cyber threats. As well as this, you can utilize network traffic behavior analytics to expose attacks that are targeting your networked systems and devices.
If you've enjoyed this article why not read A Short Guide to Security Monitoring or What is SIEM next?
