Resources
7 min read
System logging protocol, abbreviated as Syslog, is a standard protocol used for message logging. Put simply, it is a standard for collecting and storing log information. A Syslog server collects, parses, stores, examines, and dispatches log messages from devices including routers, switches, firewalls, Linux/Unix hosts, and Windows machines.
However, monitoring Syslog to derive insights is not always a straightforward process and difficulties can arise. For example, Logs from different sources will often use differing formats and terminologies, leading to a more complex analysis process. Despite the standardization offered by Syslog, the actual content and structure of log messages can vary significantly based on the source. Parsing and normalizing these logs into a unified format for analysis can be a complex task.
However, the challenges of monitoring Syslog can be alleviated with the use of a Syslog viewer which provides tools and features that streamline log management, optimize security, and simplify analysis.
Contents
What is Syslog?
Syslog is a standard protocol used for message logging. It allows various devices and software applications to ship log data to a centralized server, known as a syslog server, for monitoring and analysis. Syslog offers a way to collect and store log messages from different sources, including operating systems, network devices, and applications, in a consistent format. This centralization of log data is vital for troubleshooting, security auditing, and guaranteeing system reliability.
How Does Syslog Work?
To deepen your understanding of Syslog, here we will delve into how Syslog operates. To begin with, Syslog is made of three main components, Syslog clients, Syslog server, and Syslog messages. Syslog clients are devices or applications that generate log messages. A Syslog server is a server that receives, stores, and processes log messages from numerous clients. The server is configured to listen for incoming syslog messages, typically on UDP port 514, but it can also use TCP for more reliable communication. Lastly, Syslog messages are the log entries sent by syslog clients. Each message includes structured data, such as a timestamp, hostname, severity level, and the actual log message content.
The format of a Syslog message can be broken down further into, PRI (priority value) which is encoded within the angle brackets at the start of the message. It highlights the facility and severity level of the message. Then, the header contains the timestamp and hostname of the device that generated the log message. Lastly, MSG (message part) is the actual log message content. This can include the name of the application or process that produced the message and the log data.
Transmission of Syslog messages is a fundamental aspect of how Syslog operates, here we’ve outlined what this process involves.
Generating Log Messages: When an event occurs (such as a user login, error, or network activity), the Syslog client generates a log message.
Formatting The Message: The log message is formatted according to the Syslog standard, including the PRI, header, and MSG parts.
Sending The Message: The Syslog client ships the formatted message to the Syslog server over the network. By default, Syslog uses UDP port 514, but it can also use TCP or more secure methods like Syslog over TLS for encrypted communication.
Receiving The Message: The Syslog server listens for incoming messages on the designated port. Upon receiving a message, it processes and stores it based on predefined rules and configurations.
Storing and Analyzing: The Syslog server can store log messages in files, databases, or other storage systems. Users can then use Syslog viewers or log management tools to examine and visualize the log data, set up alerts, and generate reports.
Syslog Use Cases
As Syslog collects log messages from a broad variety of sources, the solution lends itself to numerous different use cases. Firstly, Syslog can be effectively utilized for application debugging and monitoring. By configuring applications to ship log messages to a syslog server, they can monitor application behavior, identify bugs, and track application health. This centralized logging approach helps in correlating application events with system-level logs for comprehensive troubleshooting.
In addition to this, Syslog is commonly used for network troubleshooting and performance monitoring. Network devices like routers, switches, and load balancers generate syslog messages that contain information about network performance, errors, and configuration changes. Examining these logs helps network administrators diagnose and resolve connectivity issues.
Also, numerous regulatory frameworks require organizations to maintain detailed logs of system and user activities. Syslog assists in achieving compliance by offering a standardized method for logging and retaining these records. Logs can be reviewed during audits to guarantee compliance with policies and regulations such as PCI-DSS, HIPAA, and GDPR.
Lastly, Syslog plays a vital role in security monitoring and incident response. By aggregating logs from firewalls, intrusion detection systems (IDS), and other security appliances, syslog helps in detecting suspicious activities and potential security breaches. Security teams can analyze these logs to identify and respond to threats promptly.
Syslog Best Practices
Having provided a complete overview of Syslog, to further your understanding, it’s important to know some of the best practices and tips for Syslog. To begin with, you should include syslog severity levels when sending a message. It is essential for prioritizing events, granular filtering and routing, gaining operational insights, maintaining standardization, and facilitating troubleshooting. It optimizes the efficiency and effectiveness of log management and analysis processes across your organization's IT environment.
As well as this, another useful tip when using Syslog is to implement filtering mechanisms to route logs to the appropriate destinations based on their content or severity. Use syslog-ng or rsyslog configurations to outline filters and actions, such as writing logs to different files, shipping them to remote syslog servers, or triggering alerts. This helps in handling log volume and guaranteeing that critical events are promptly addressed.
Lastly, another crucial practice is to monitor the health and performance of your syslog infrastructure to guarantee the reliability and timely delivery of log messages. Track syslog server resources such as CPU, memory, disk I/O, and network bandwidth to detect potential bottlenecks or performance issues. Execute proactive alerting mechanisms to notify administrators of any syslog-related issues promptly.
Why You Should Use A Syslog Viewer
Utilizing a Syslog viewer can alleviate some of the difficulties of monitoring Syslog. In addition to this, a Syslog viewer offers its own set of advantages for organizations. Firstly, a Syslog viewer aggregates log data from numerous sources into a single interface, streamlining the management and organization of logs. This centralization makes it simpler to track and access logs from various devices and applications, lessening the complexity of log management.
In addition to this, Syslog viewers allow for real-time monitoring of log messages, enabling users to detect and respond to issues promptly. They can be configured to produce alerts based on specific criteria, such as certain keywords, severity levels, or patterns in log data. This proactive approach assists in highlighting and mitigating problems before they escalate.
Continuing with the advantages that Syslog viewers provide, these tools are designed to manage large volumes of log data, making them suitable for environments of any size, from small businesses to large enterprises. They can effectively scale to accommodate increasing amounts of data without compromising performance, guaranteeing that organizations can continue to track and examine logs effectively as their infrastructure expands.
The Leading Syslog Viewers
SolarWinds
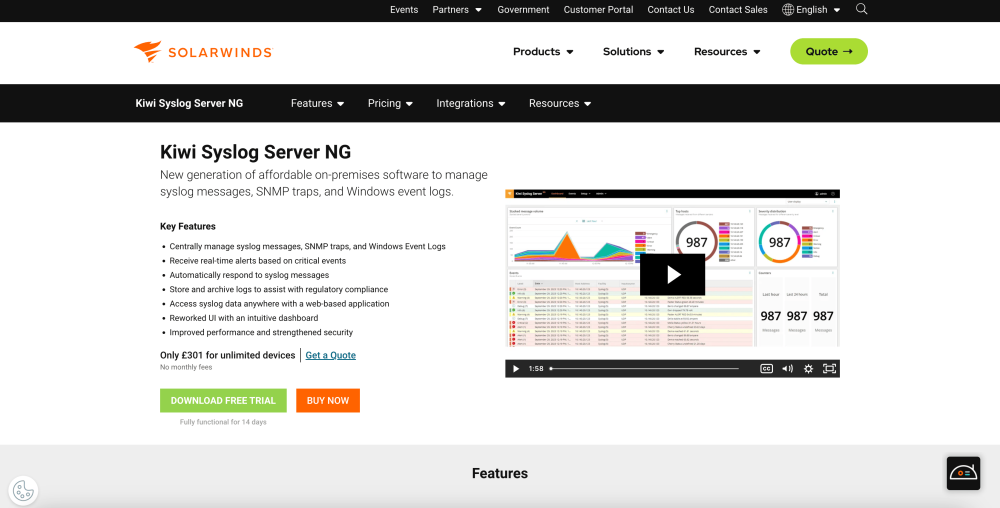 SolarWinds offers Kiwi Syslog Server NG, a Syslor viewer that can collect Syslog messages from a variety of equipment types, including routers, computers, and firewalls. With this tool, you can filter out irrelevant messages and apply rules to notify you when an issue is detected almost in real-time. As well as this, SolarWinds solution enables you to archive syslog messages to help meet the expectations of your security team.
SolarWinds offers Kiwi Syslog Server NG, a Syslor viewer that can collect Syslog messages from a variety of equipment types, including routers, computers, and firewalls. With this tool, you can filter out irrelevant messages and apply rules to notify you when an issue is detected almost in real-time. As well as this, SolarWinds solution enables you to archive syslog messages to help meet the expectations of your security team.
Logit.io
 The Logit.io Syslog viewer, simplifies the analysis of Syslog data by aggregating logs from various sources into a single, centralized location. This tool converts all messages into a structured logging format, optimizing the ability to sort and search through log files. This is particularly beneficial when managing data from diverse systems and applications. With Logit.io’s solution, you can establish alerts that scan for log entries and messages that meet specific criteria, this could be an error or a security incident, to instantly send a notification to your engineering team.
The Logit.io Syslog viewer, simplifies the analysis of Syslog data by aggregating logs from various sources into a single, centralized location. This tool converts all messages into a structured logging format, optimizing the ability to sort and search through log files. This is particularly beneficial when managing data from diverse systems and applications. With Logit.io’s solution, you can establish alerts that scan for log entries and messages that meet specific criteria, this could be an error or a security incident, to instantly send a notification to your engineering team.
If you want to learn more about Logit.io’s Syslog viewer and its extensive capabilities and benefits that it can offer to your organization, don’t hesitate to contact us or begin exploring the platform for yourself with a 14-day free trial.
Datadog
 Whilst Datadog does not offer a dedicated Syslog viewer, its log management solution is powerful and can be used in such a way. With this solution, you can utilize out-of-the-box log processing pipelines for 200+ common technologies.
Whilst Datadog does not offer a dedicated Syslog viewer, its log management solution is powerful and can be used in such a way. With this solution, you can utilize out-of-the-box log processing pipelines for 200+ common technologies.
If you've enjoyed this article, why not read Everything You Need To Know About Log Viewers or The Top 60 Log Management Tools next?