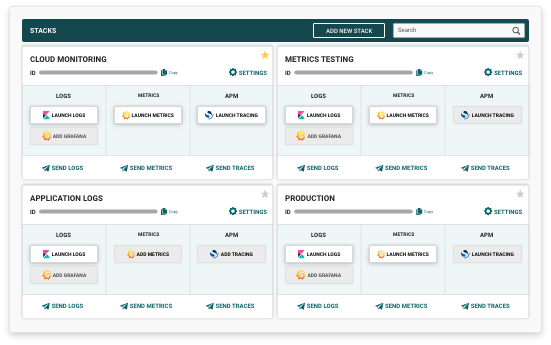
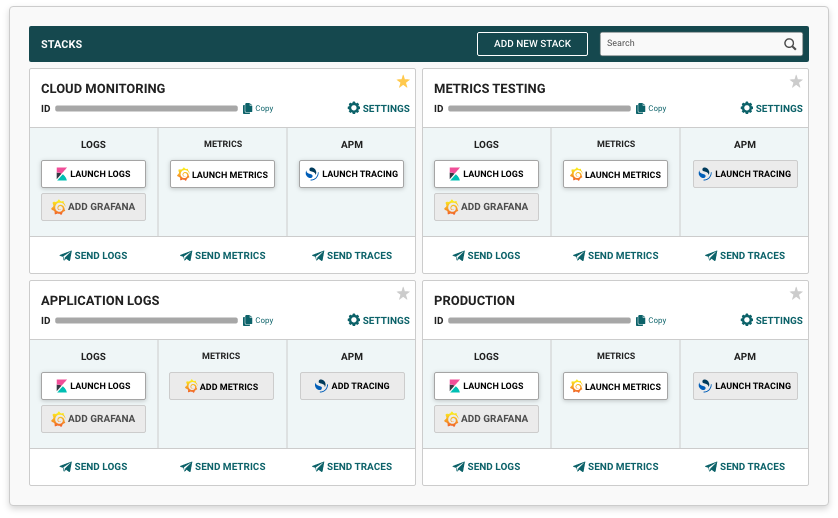
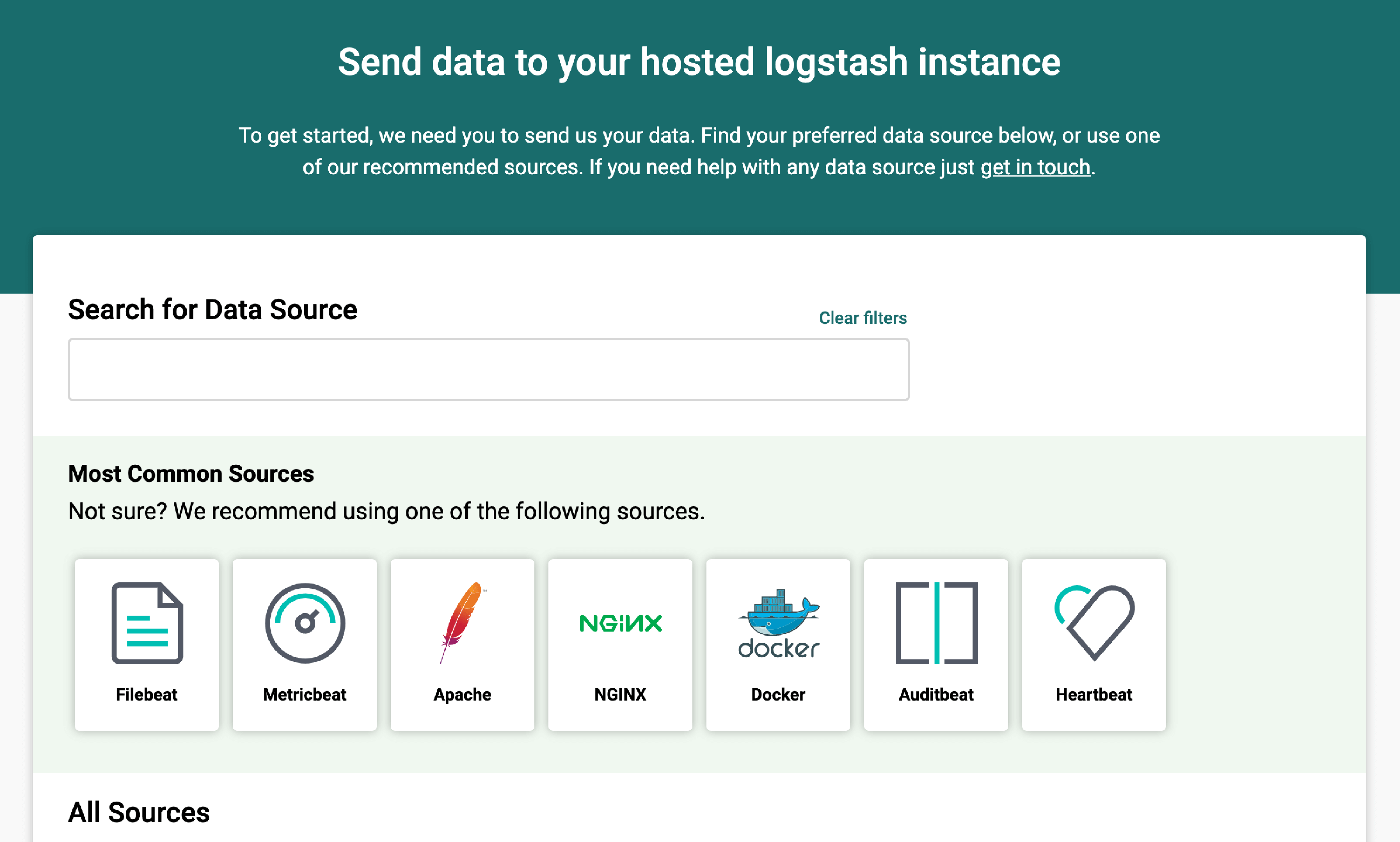
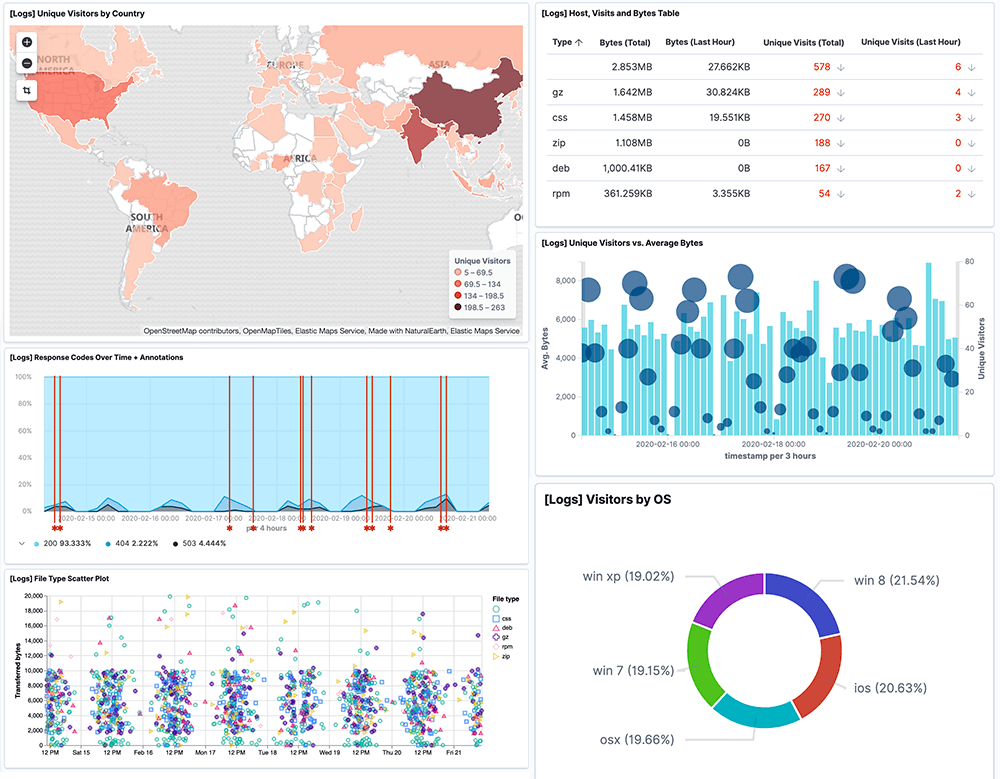
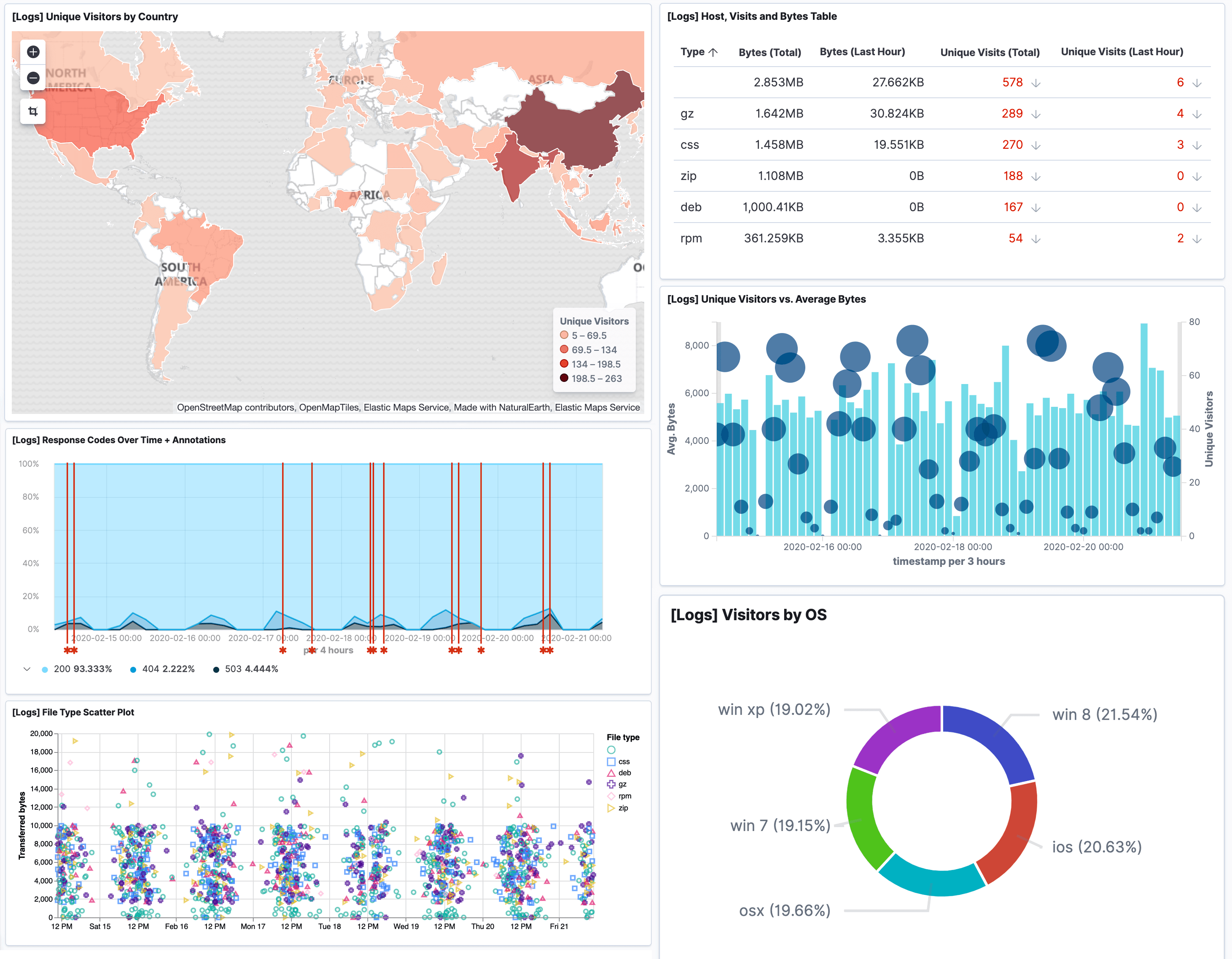
Correlate your event logs and identify threats and suspicious activity in real-time with the Logit.io event log analyser, provided as part of our scalable managed ELK & Grafanaplatform.
Event log analysis can be used to identify numerous security incidents from being able to audit user access and isolate attacks affecting your web servers through to monitoring malicious traffic and isolating monitor rule changes on your Firewall.
By using our event log analyser for reporting, alerting, monitoring and data visualisation, you'll gain a centralised view of the health and security of your applications and services in a single affordable and scalable platform.
Our cloud-native platform is built on the highly available open source tools Elasticsearch, Logstash, Kibana & Grafana to provide you with all of the benefits without the costs, upgrades and implementation issues commonly associated with build you own deployments.
Our platform is also fully compliant when used as a Windows event log analyser and is cross compatible with a wide range of other operating systems, services and third party services.