It is estimated that there is around a 1 in 3 risk of any small to medium business experiencing a cyber security breach in the next year. The likelihood of suffering a breach only increases as your business grows in size and complexity.
In the event a breach does occur it is necessary to use specialised tools that allow you to identify both the areas of your infrastructure that are most vulnerable and also pinpoint the origins of an attack.
Without knowing what has occurred, what is the impact and what steps need to be taken in order to avoid a repeat of the incident, you'll leave your operations unsecured and the chances of an attack occurring in the future only increase.
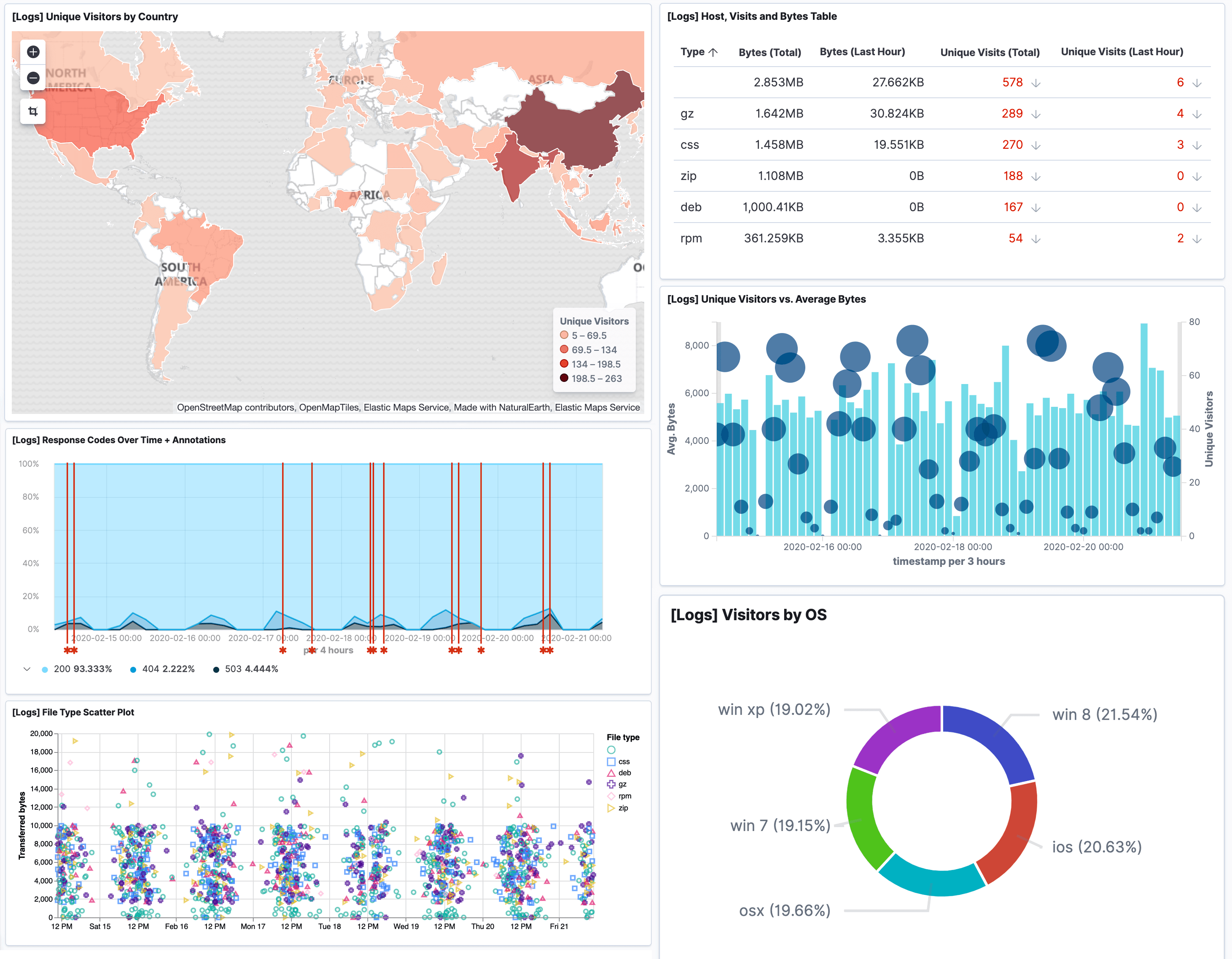
By reviewing logs you can often quickly identify the events leading up to a cyber security incident by simply analysing system security and application events. Log files are created by operating systems, servers, programming tools and third party tools.
Logging made easy from Logit.io can be set up within minutes to strengthen your organisation's cyber security, compliance and data protection capabilities. By providing a platform that ensures a unified view of operations via our centralised logging solution we make gathering, parsing and enriching your raw log files for reporting, monitoring and analysis simple, easy and affordable.